我使用的操作系统是Windows10。

openssl 下载地址: https://mirror.firedaemon.com/OpenSSL/openssl-3.0.2.zip
下载的网站是: https://kb.firedaemon.com/support/solutions/articles/4000121705
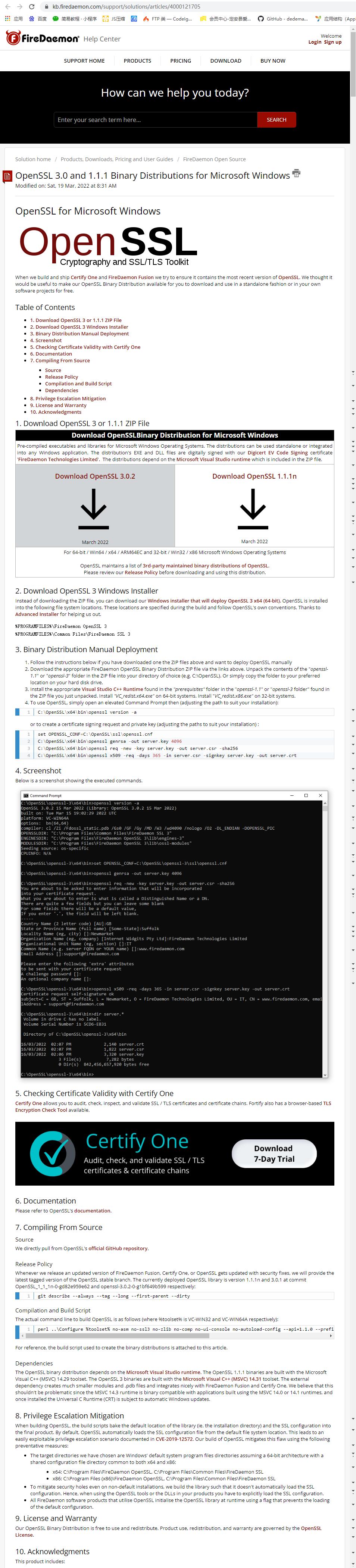
安装包解压后的目录结构:
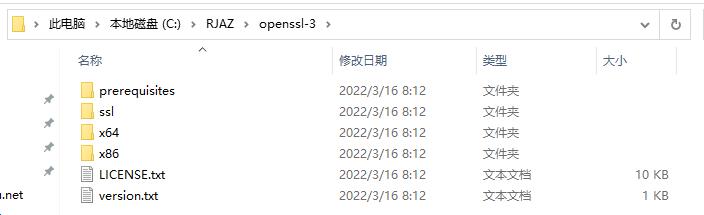
然后设置环境变量:
path变量设置的是用户的,如图是admin用户的,不是设置系统的path变量
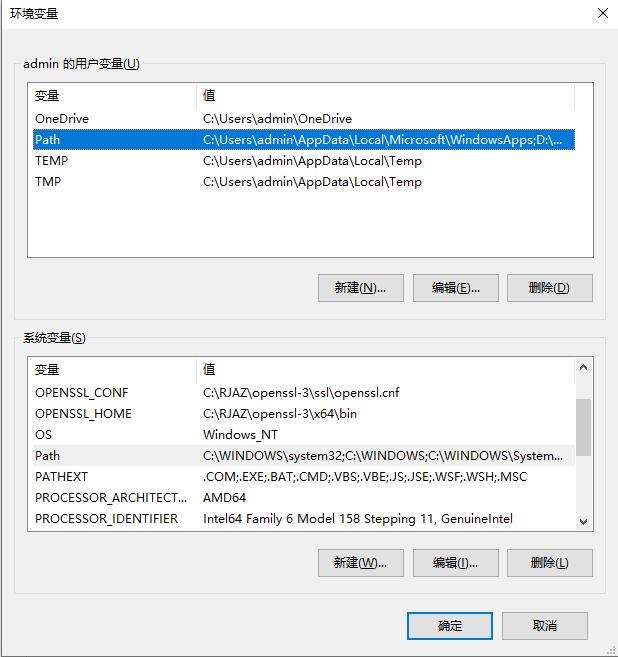
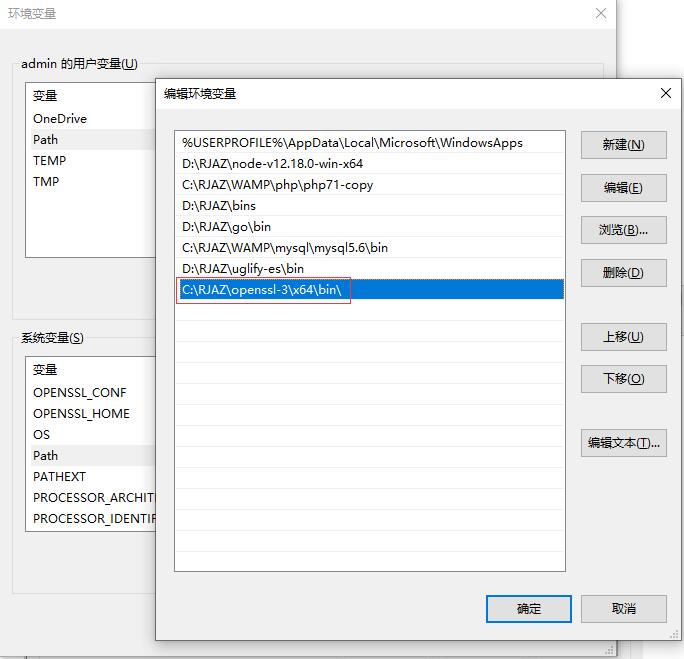
设置的这个路径: C:\RJAZ\openssl-3\x64\bin\ ,该路径下的文件结构:
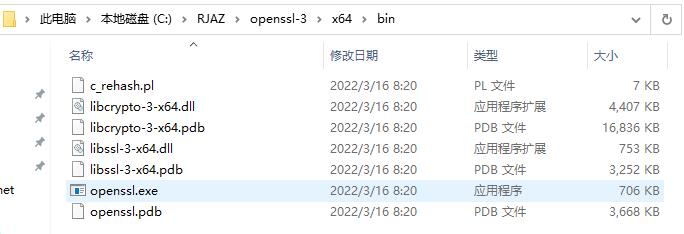
然后在系统变量里添加两个变量,OPENSSL_HOME 和 OPENSSL_CONF
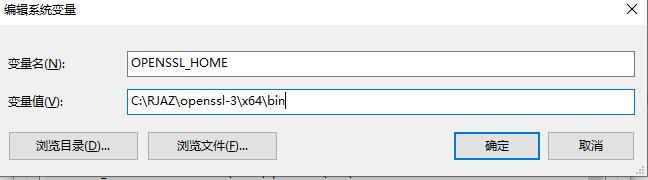
OPENSSL_HOME 变量的值设置为: C:\RJAZ\openssl-3\x64\bin
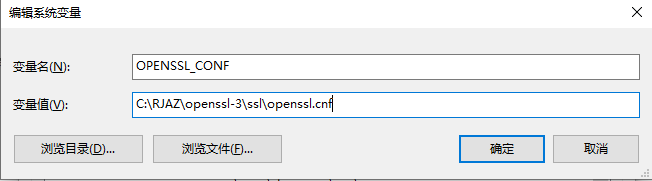
OPENSSL_CONF 变量的值设置为: C:\RJAZ\openssl-3\ssl\openssl.cnf
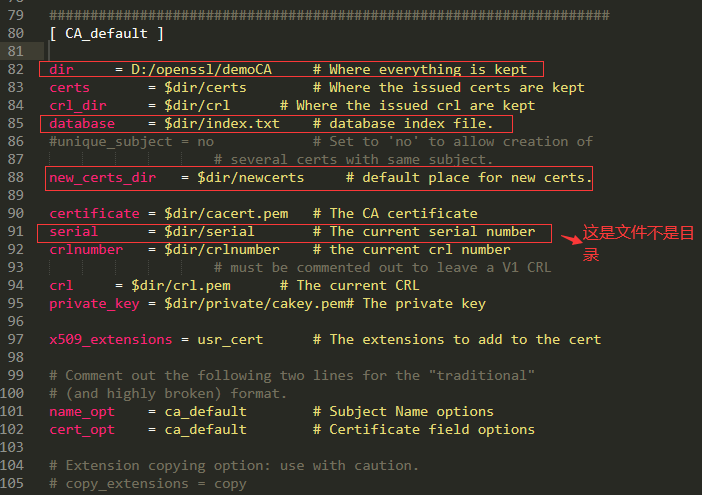
C:\RJAZ\openssl-3\ssl\openssl.cnf ,这个配置文件需要用到
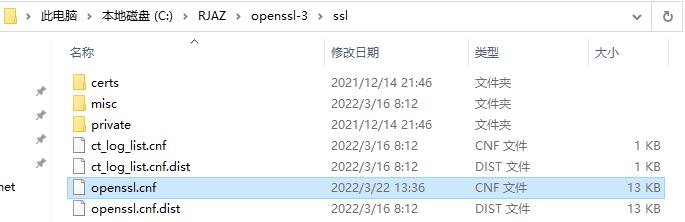
openssl.cnf这个配置文件内容部分截图:

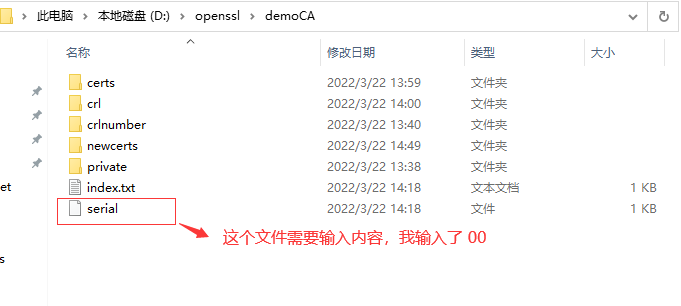
serial 文件不存在时出现错误:
D:/openssl/demoCA/serial: Permission denied
38270000:error:80000005:system library:BIO_new_file:Input/output error:..\crypto\bio\bss_file.c:67:calling fopen(D:/openssl/demoCA/serial, r)
38270000:error:10080002:BIO routines:BIO_new_file:system lib:..\crypto\bio\bss_file.c:77:
error while loading serial number
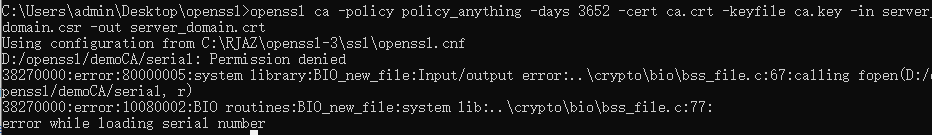
serial 存在但是这个文件内容为空的话会出现错误:
Using configuration from C:\RJAZ\openssl-3\ssl\openssl.cnf
Unable to load number from D:/openssl/demoCA/serial
48250000:error:06800096:asn1 encoding routines:a2i_ASN1_INTEGER:short line:..\crypto\asn1\f_int.c:139:
error while loading serial number
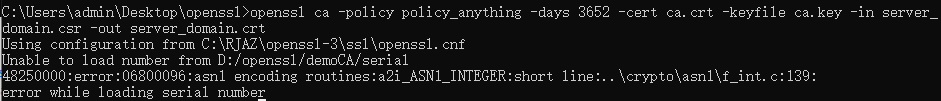
接下来输入指令生成证书,我从网上收集了测试指令,参考链接( https://its401.com/article/qq_28938933/88832306 )
★★签发命令
(1)生成自己的根证书
##生成根CA密钥
openssl genrsa -out ca.key 2048
##生成CA根证书
openssl req -new -x509 -days 7304 -key ca.key -out ca.crt -subj "/C=CN/ST=shandong/L=jinan/O=My SSL G1/OU=IT Dept/CN=My SSL G1 Server"
(2)生成服务器证书密钥及证书签发
##生成SSL证书私钥:
openssl genrsa -out server_domain.pem 2048
##制作SSL证书私钥
openssl rsa -in server_domain.pem -out server_domain.key
##生成SSL证书请求
openssl req -new -key server_domain.pem -out server_domain.csr -subj "/C=CN/ST=shandong/L=jinan/O=my domain test/OU=IT Dept/CN=my domain"
##根CA进行SSL证书签发
openssl ca -policy policy_anything -days 3652 -cert ca.crt -keyfile ca.key -in server_domain.csr -out server_domain.crt
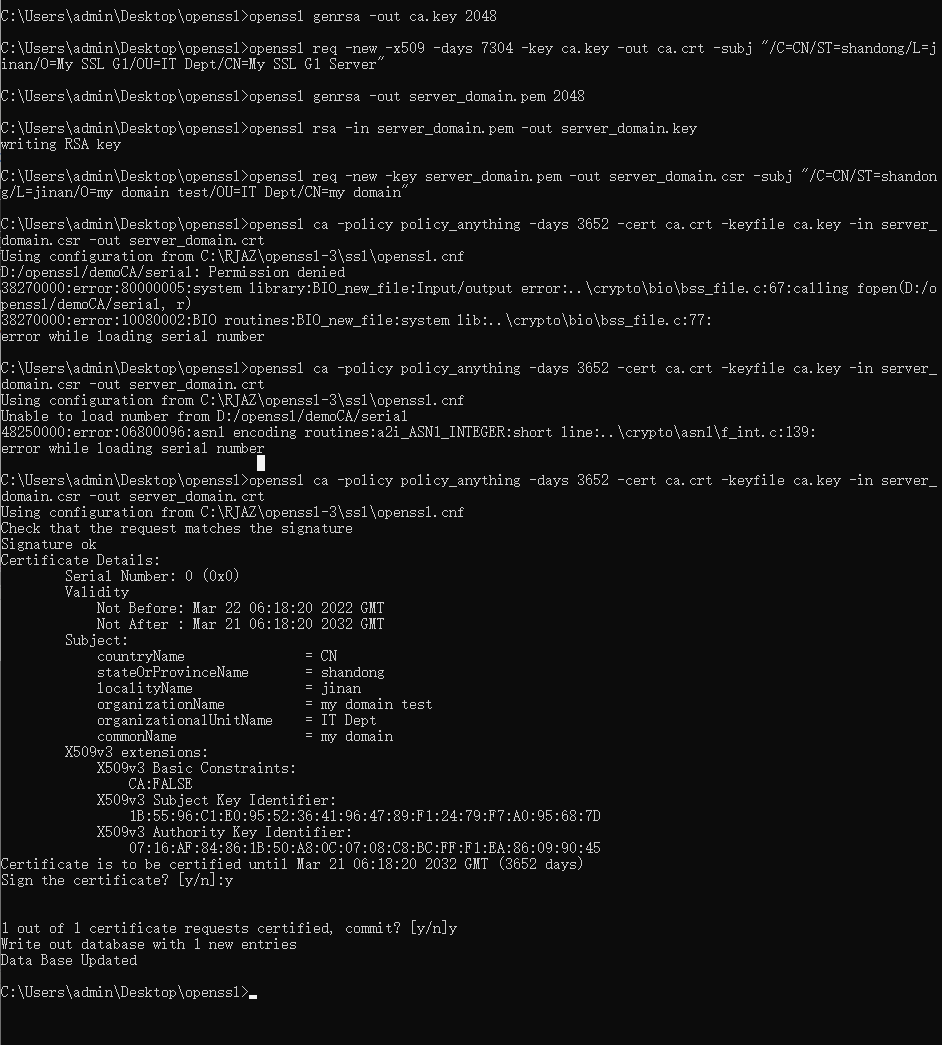
ok,完成了。
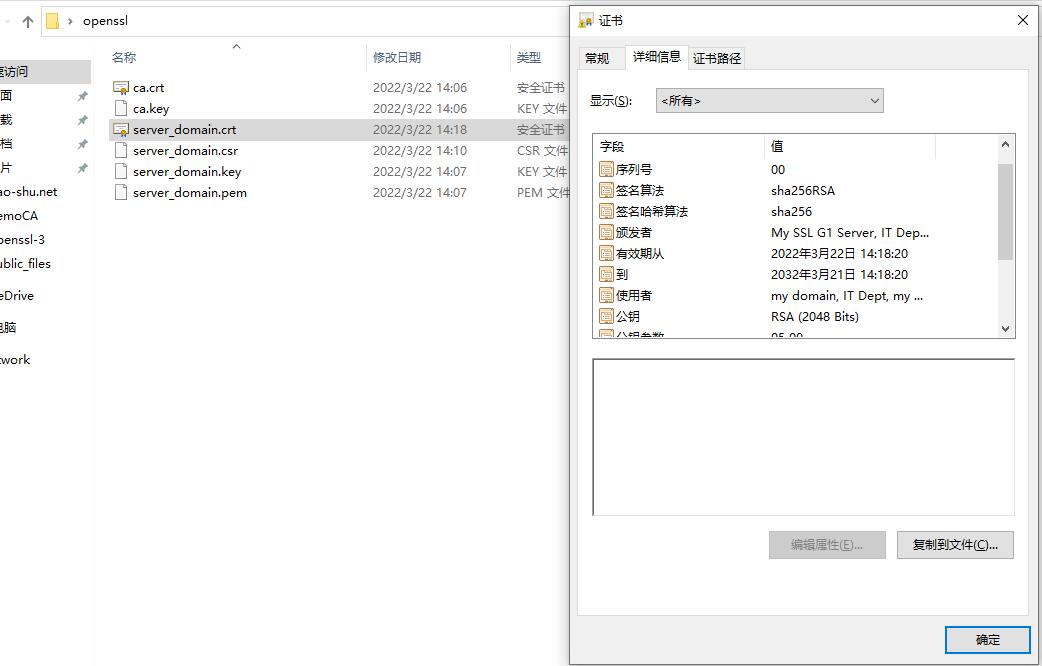
2022-03-24 更新,让谷歌浏览器不报警“不安全”
我继续在网上收集了一些资料,整理一下,我写了个bat文件脚本如图:
生成ca根证书.bat ,内容如下:
@echo off
::生成ca秘钥,得到ca.key
openssl genrsa -out ca.key 4096
pause
::生成ca证书签发请求,得到ca.csr
openssl req -new -sha256 -out ca.csr -key ca.key -config ca.conf
pause
::生成ca根证书,得到ca.crt
openssl x509 -req -days 3650 -in ca.csr -signkey ca.key -out ca.crt
pause
如图:
执行脚本之前,先配置 ca.conf 这个文件,这个文件内容为:
[ req ]
default_bits = 4096
distinguished_name = req_distinguished_name
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = HaiNan
localityName = Locality Name (eg, city)
localityName_default = HaiKou
organizationName = Organization Name (eg, company)
organizationName_default = Fang
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64
commonName_default = Fang Root SSL
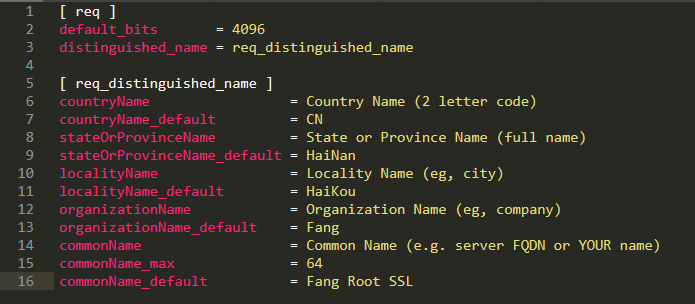
配置好后执行脚本,一路回车就行了,配置文件可以根据自己的需求更改。
接下来是 生成终端用户证书.bat 这个脚本文件内容:
@echo off
::生成秘钥,得到server.key
openssl genrsa -out server.key 2048
pause
::生成证书签发请求,得到server.csr
openssl req -new -sha256 -out server.csr -key server.key -config server.conf
pause
::用CA证书生成终端用户证书,得到server.crt
openssl x509 -req -days 732 -CA ca.crt -CAkey ca.key -CAcreateserial -in server.csr -out server.crt -extensions req_ext -extfile server.conf
pause
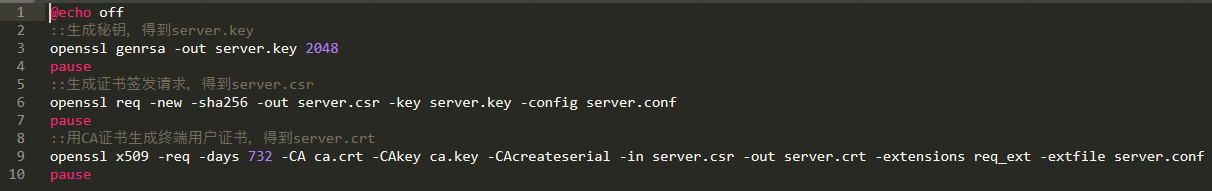
配置文件 server.conf 的内容为:
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
req_extensions = req_ext
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = HaiNan
localityName = Locality Name (eg, city)
localityName_default = HaiKou
organizationName = Organization Name (eg, company)
organizationName_default = Fang
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64
commonName_default = *.test2022.cn
[ req_ext ]
subjectAltName = @alt_names
[alt_names]
DNS.1 = xx1.test2022.cn
DNS.2 = xx2.test2022.cn
DNS.3 = xx3.test2022.cn
DNS.4 = xx4.test2022.cn
IP.1 = 192.168.1.51
IP.2 = 192.168.1.101
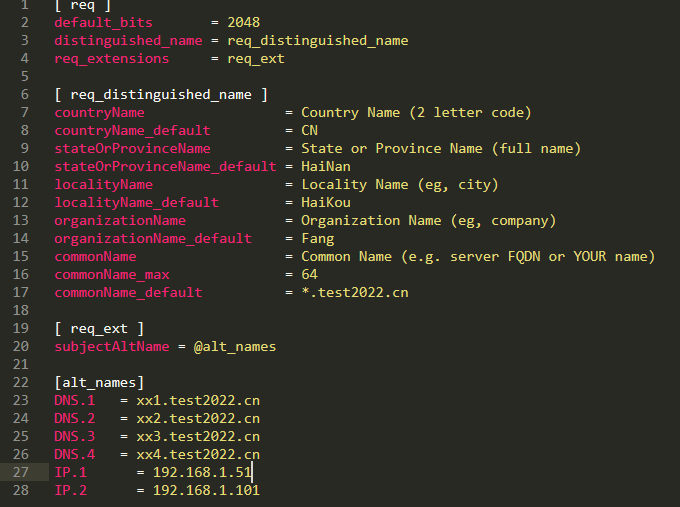
配置好后执行脚本,一路回车就可以了。
需要右键ca.crt安装,安装到“受信任的根证书颁发机构”(不然server.crt还是不受信任的)
参考的链接:
https://www.cnblogs.com/nidey/p/9041960.html
https://www.cnblogs.com/will-space/p/11913744.html
后续有时间再整理更新![]() 。
。